Reachability Analysis for Vulnerable Packages
Introduction
Software applications often depend on third-party libraries and packages, which may contain security vulnerabilities. While security scanners can detect these vulnerabilities, not all of them pose an immediate risk. Reachability analysis helps determine whether a vulnerable package is actually used in the codebase.
- Reachable vulnerability: The vulnerable code is executed somewhere in the application.
- Unreachable vulnerability: The vulnerable package is installed but never used in the execution flow.
This approach helps security teams prioritize which vulnerabilities need immediate action, reducing false alarms and focusing on real risks.
Why Reachability Analysis is Important?
- ✅ Reduces False Positives: Not all installed vulnerable packages affect the application.
- ✅ Prioritizes Risk Mitigation: Focuses on vulnerabilities that can actually be exploited.
- ✅ Optimizes Security Efforts: Helps developers avoid unnecessary patching for unused vulnerabilities.
- ✅ Improves Compliance: Ensures security teams can justify risk acceptance for unreachable vulnerabilities.
Reachability analysis helps differentiate between critical security threats and theoretical risks, improving vulnerability management.
How Reachability Analysis Works?
1. Identify Installed Vulnerable Packages
Use the Flyingduck agent to scan the repository via workflows, pipelines, or runners. The identified results will be reported to the Flyingduck portal.
By default rechanility analysis is disabled. So, to enable this make sure RA=true present in the respective flows.
-e RA=true \ in the evironmental variables.2. Determine Reachability Status
ReachableA vulnerability is reachable if the package is used in the code.
Not ReachableA vulnerability is not reachable if the package is installed but unused.
UnknownFlyingduck has not performed Reachability Analysis.
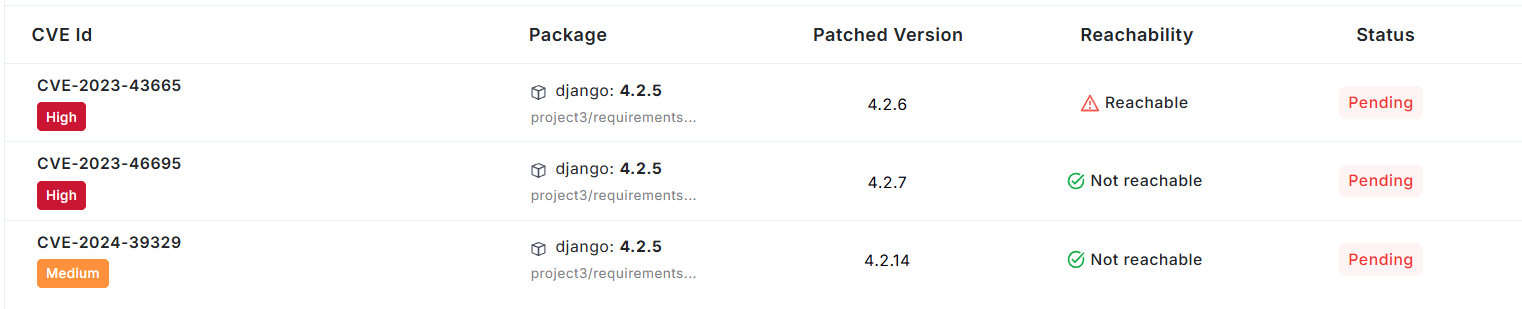
3. Take Action Based on Reachability
- If reachable:
- 🔴 High priority → Patch or replace the package immediately.
- 🛡 Mitigation → Apply security controls (e.g., sandboxing, input validation).
- If not reachable:
- 🟡 Lower priority → Plan patching in future releases.
- 📊 Monitor changes → Ensure the package is not used later.
- ♻ Remove unnecessary dependencies → Reduce attack surface.
Conclusion
Reachability analysis enhances vulnerability management by ensuring that security teams focus on real risks rather than theoretical threats. By distinguishing between reachable and unreachable vulnerabilities, organizations can prioritize patching efforts, reduce noise, and improve security efficiency.